Key Takeaways
- Enterprise web development is crucial for increasing sales and customer engagement.
- Well-designed user interfaces (UI) and user experiences (UX) significantly boost conversion rates.
- Web applications are frequent targets of security breaches, making security a critical focus.
- Reliable enterprise web solutions rely on solid frontend architecture, efficient backend systems, and strategic database selection.
- Component-based architecture is essential for maintainability and team collaboration in frontend development.
- Efficient handling of workloads, scalability through horizontal scaling, and multi-tier architecture are vital for backend systems.
- Choosing the right database involves considering data volume, accessibility, flexibility, security, and performance.
- Building scalable, secure, and high-performing applications is essential for long-term success.
Enterprise web development is more than just a necessity—it’s a game-changer. 90% of companies report increased sales and customer engagement after investing in enterprise web development.
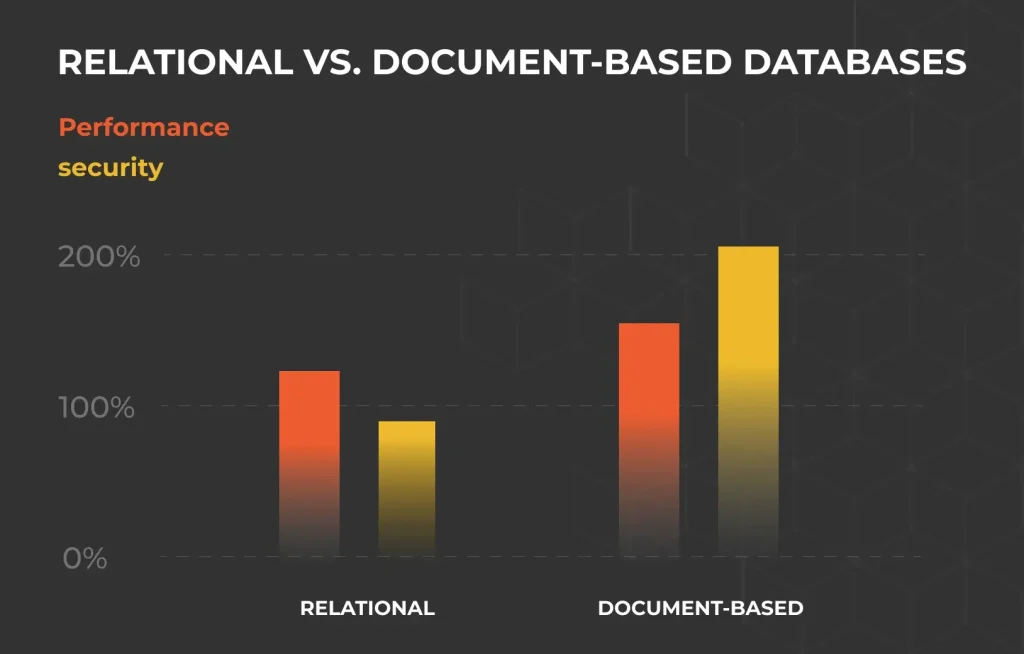
The numbers speak for themselves. Research from Forrester shows that a well-designed UI can boost conversion rates by 200%, while an improved UX can drive them up by 400%.
But success isn’t just about aesthetics; security is paramount.
According to Verizon’s Data Breach Investigations Report, web applications were the target in 43% of security breaches in 2020—more than double the previous year.
To stay competitive, your enterprise web solution must be scalable, secure, and seamlessly integrated with essential business tools like CRMs and ERPs.
We’ll walk you through the key strategies for building enterprise web applications that drive real results.
Core Components of Enterprise Web Solutions

Building reliable enterprise web solutions depends on three main components that combine smoothly. Let’s get into each component’s vital requirements to create flexible applications.
Frontend Architecture Requirements
A well-laid-out frontend architecture creates the foundation of enterprise web solutions. Note that component-based architecture encapsulates features that become shareable among other modules and offer better control with faster development.
On top of that, it helps to break down complex frontend code into reusable components to improve maintainability and promote efficient team collaboration.
Backend System Design
The backend system powers enterprise web applications.
Heavy workloads need efficient handling because of increased data volume and multiple simultaneous requests. More servers and nodes allow the distribution of queries through horizontal scaling, which reduces the load on a single server.
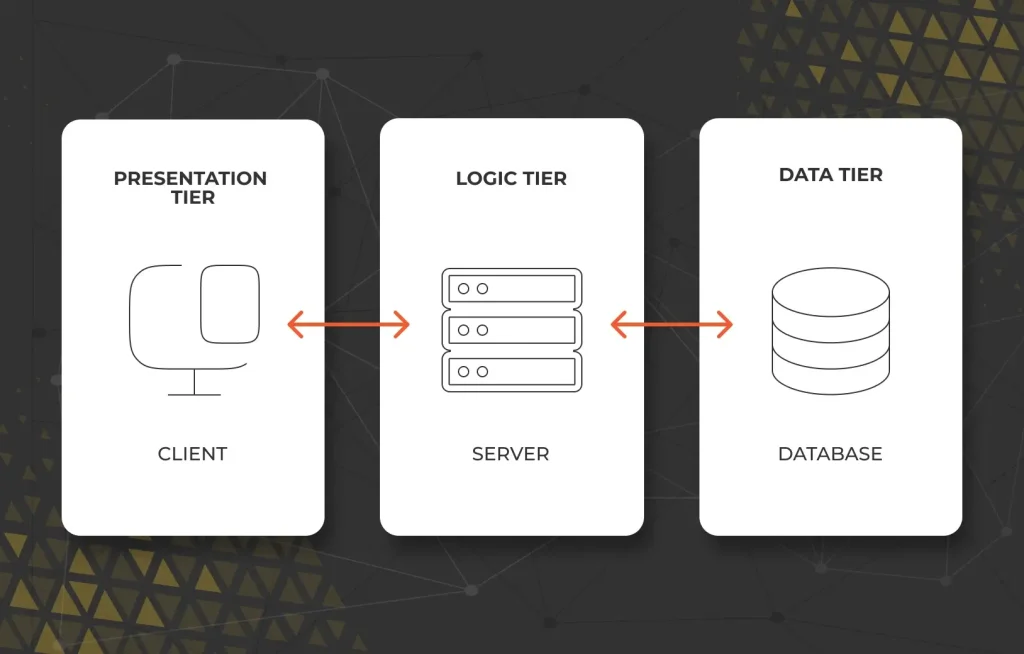
Large-scale web application architecture works with a multitier approach that consists of three separate modules: the client-side server, application server, and database server. Each layer performs its simple functions without overload, which leads to better performance and maintainability.
Database Selection Criteria
Database selection plays a vital role in enterprise applications. Research indicates web applications attract security attacks, with all but one of these breached assets occurring in database systems.
Think over these essential factors while choosing a database:
- Data volume and accessibility requirements
- Structure flexibility and scalability needs
- Security measures and data protection capabilities
- Performance optimization capabilities
Oracle and PostgreSQL offer great support to enterprises handling structured data with ACID (Atomicity, Consistency, Isolation, and Durability) transactions.
Document stores like MongoDB excel with semi-structured and unstructured data management and provide flexibility in document structure without affecting other documents.
Building a Scalable Technical Foundation
Scaling enterprise web applications needs a strong technical foundation built on three essential pillars: load balancing, efficient caching, and strategic database management.
Load Balancing Implementation
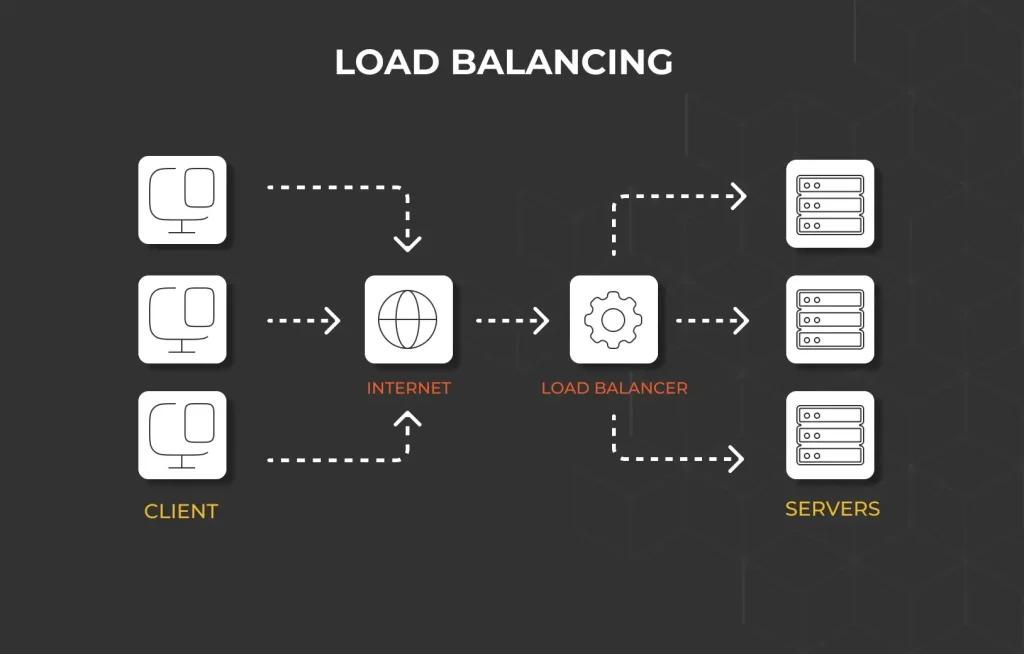
Load balancing spreads incoming network traffic across multiple servers to prevent any single server from getting overwhelmed. A properly configured load balancer works as a reverse proxy that handles client requests and protects back-end servers from direct attacks.
Modern load-balancing systems use these distribution algorithms:
- Round-robin to distribute traffic sequentially
- Least connections method to optimize server utilization
- IP hash to maintain consistent client-server mapping
- Weighted response time to route based on performance
Caching Strategies
Smart caching substantially reduces database queries and speeds up response times. In-memory caching systems like Redis or Memcached store frequently accessed data and cut down the need to fetch information repeatedly from the source.
Cache expiration times help prevent stale data issues. Setting the right Time-To-Live (TTL) values will give a perfect balance between data freshness and optimal performance.
Redis Cluster and other distributed caching solutions make it possible to scale across multiple nodes, which boosts system resilience and performance.
Database Sharding Approaches
Database sharding tactics split data volumes into discrete, manageable segments. While this method increases system complexity, it unlocks unlimited scaling potential for data-heavy operations.
Enterprise applications benefit from four proven sharding methods. Range-based approaches create predictable data segments through value boundaries. Hash-based distribution ensures even data spread, while entity sharding maintains logical data relationships.
Geographic distribution optimizes access speeds based on user locations.
Successful technical foundations require vigilant monitoring systems. Regular health assessments trigger automatic traffic redirection when performance issues arise. This proactive approach guarantees high availability while building resilient systems ready for growing enterprise demands.
Security Implementation Framework
Security architecture forms the bedrock of enterprise web applications. Two critical pillars support this foundation: robust authentication systems and comprehensive data encryption protocols.
Authentication System Design
Enterprise applications demand sophisticated user verification systems. Multi-factor authentication (MFA) stands out as a proven security measure, slashing account compromise incidents by 99.9%.
Effective MFA deployment combines multiple verification layers:
- Standard password protection
- Time-sensitive one-time codes (TOTPs)
- Biometric identity checks
- Secondary channel verification
Role-based access control (RBAC) creates precise boundaries around user permissions. This system maps specific roles to job functions, establishing clear access parameters. JWT authentication enhances this framework, enabling stateless verification while boosting system scalability.
Data Encryption Standards
Strong encryption protocols shield enterprise data through sophisticated cryptographic techniques. Industry leaders trust AES and RSA algorithms for their proven track records in symmetric and asymmetric encryption.
Robust encryption must protect data across three critical states:
- Active transmission protection
- Storage security measures
- Complete lifecycle safeguards
Enterprise key management requires meticulous attention. Successful systems incorporate secure key creation, storage protocols, distribution methods, and rotation schedules. Hardware Security Modules (HSMs) and cloud-based solutions provide additional protection layers.
NIST encryption guidelines set industry benchmarks. Their SP 800-52 protocol details TLS implementation requirements, while SP 800-111 outlines storage encryption standards. These frameworks ensure alignment with GDPR, HIPAA, and PCI-DSS requirements.
Security systems demand constant vigilance. Regular assessments identify vulnerabilities, while timely updates address emerging threats. This proactive stance maintains robust protection against evolving security challenges.
Performance Optimization Techniques
Performance optimization determines the success of enterprise web applications. Three strategic focus areas ensure peak application performance across diverse user scenarios.
Code Splitting Methods
Code splitting elevates application performance through strategic source code segmentation. Smart partitioning of JavaScript applications creates separate downloadable bundles, reducing initial page load bottlenecks.
Dynamic imports excel in enterprise environments. Strategic use of import() syntax enables precise module loading based on user needs. This targeted approach shrinks initial JavaScript payloads while boosting startup speed and user interaction metrics.
Asset Optimization
Asset optimization shapes user experience quality in enterprise applications. Studies show targeted performance improvements directly enhance page speeds and user satisfaction by eliminating technical inefficiencies.
Key optimization protocols include:
- HTTP request reduction through file consolidation
- Strategic browser cache implementation
- Code minification across CSS, JavaScript, and HTML
- Quality-focused image compression
Image assets deserve particular scrutiny as primary bandwidth consumers. Tools like Squoosh enable precise image optimization while preserving visual fidelity.
CDN Implementation Strategy
Content Delivery Networks redefine digital content distribution methods. Strategic server placement across global locations minimizes latency while maximizing bandwidth efficiency.
Successful CDN deployment requires precise configuration. Content distribution systems manage asset placement while intelligent routing directs requests to optimal endpoints. Smart traffic distribution mechanisms balance server loads effectively.
Enterprise CDN strategies prioritize localized content delivery. This focus protects against network congestion while ensuring consistent service quality.
Successful implementations align CDN capabilities with existing infrastructure and DevOps workflows.
Testing and Quality Assurance
Quality assurance protocols determine the reliability of enterprise web applications. Strategic testing procedures validate application performance across diverse operational scenarios.
Load Testing Procedures
Load testing measures system resilience under real-world conditions. LoadRunner Enterprise tools enable precise performance simulation and metric tracking. Critical measurement points include:
- Response timing patterns and peaks
- System throughput and transaction rates
- Network delay indicators
- User concurrency thresholds
- Resource consumption patterns
Successful load testing starts with precise objective definition and parameter setting. Systematic load progression reveals system bottlenecks. Performance analytics guide targeted infrastructure enhancements.
Security Testing Protocol
Security testing safeguards systems against malicious actors and internal vulnerabilities. Thorough security protocols examine every defensive layer within the application architecture.
OWASP testing frameworks establish structured security evaluation methods. Active threat analysis identifies technical weaknesses before they become exploitable vulnerabilities. Scheduled security reviews maintain regulatory compliance while protecting sensitive information.
Dual-layer security assessment combines automated scanning with expert penetration testing. This methodology catches both common security gaps and sophisticated vulnerabilities that escape automated detection.
Integration Testing Approach
Integration testing validates component interoperability within complex systems. Precise planning ensures thorough coverage across all system interactions.
Effective testing strategies blend automated efficiency with human insight. While automation tools deliver speed and consistency, manual testing uncovers nuanced scenarios. Netflix’s 2021 outage highlights this need – seemingly independent services failed despite passing unit tests.
Key integration testing focus areas include:
- Interface compatibility verification
- Data flow validation
- System functionality assessment
- Integrated performance evaluation
Continuous integration testing catches issues during development. CI/CD pipeline integration maintains quality standards while supporting rapid delivery cycles.
Future-Proof Your Enterprise Web Development with Fahrenheit Marketing
Your enterprise application deserves a foundation that can scale, perform, and stay secure in an ever-evolving digital landscape.
With strategic architecture, advanced security protocols, and performance-driven engineering, you can build a system that truly delivers measurable business impact.
Need expert guidance to develop a high-performance enterprise web solution?
Partner with Fahrenheit Marketing today and turn your digital vision into reality.
